Security Information and Event Management (SIEM) Solutions
Category: Cyber Security
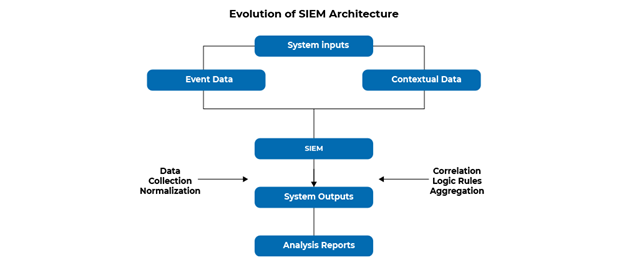
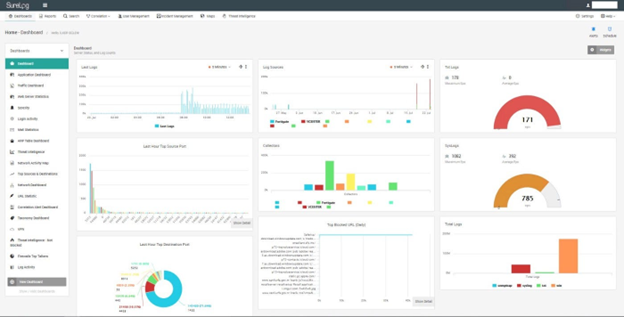
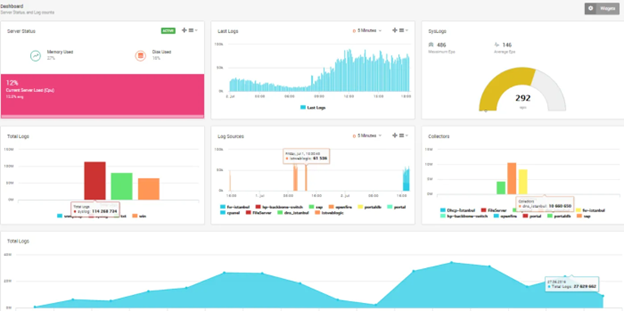
Project Overview
This project involves deploying and managing advanced Security Information and Event Management (SIEM) solutions for multiple customers in Sydney. The aim is to provide comprehensive security monitoring, threat detection, and incident response capabilities tailored to the specific needs of each client. Our expertise includes SIEM solutions such as Wazuh, IBM Splunk, Microsoft Sentinel, Fortinet, Elastic Security, SIEM Monster, and more.
Project Phases
Phase 1: Initial Assessment and Planning
- Requirement Analysis
- Stakeholder Meetings : Conduct meetings with key stakeholders to understand their security requirements, existing infrastructure, and specific needs.
- Current Security Posture Review : Assess the current security posture, including existing monitoring solutions and identified threats.
- Project Scope Definition
- Scope and Objectives : Define the project scope, objectives, timelines, and responsibilities.
- Compliance and Security : Ensure compliance with relevant industry regulations and security standards.
Phase 2: Solution Design and Preparation
- SIEM Solution Selection
- Vendor Evaluation : Evaluate SIEM solutions from Wazuh, IBM Splunk, Microsoft Sentinel, Fortinet, Elastic Security, SIEM Monster, and others to select the best fit for the organization’s needs.
- License Procurement : Procure the necessary licenses for the chosen SIEM solution.
- Infrastructure Preparation
- Network Readiness : Ensure network readiness, including IP address allocation, firewall settings, and VPN configurations if required.
- Data Source Inventory : Identify and inventory all data sources (servers, applications, network devices) that will be integrated with the SIEM solution.
Phase 3: SIEM Solution Deployment
- SIEM Installation
- Server Setup : Set up servers for the SIEM solution, including necessary hardware and virtual machines.
- Software Installation : Install the SIEM software on designated servers.
- Data Source Integration
- Log Collection : Configure log collection from various data sources such as servers, network devices, applications, and cloud services.
- Log Parsing : Set up log parsing rules to normalize data from different sources.
- Centralized Management Console Setup
- Console Configuration : Set up and configure the centralized management console for monitoring and managing the SIEM solution.
- Role-Based Access Control : Implement role-based access control (RBAC) to restrict access based on user roles and responsibilities.
Phase 4: Security and Compliance
- Security Configuration
- Correlation Rules : Develop and configure correlation rules to detect complex threats and suspicious activities.
- Automated Response : Set up automated response actions, such as alerting, isolation, and remediation, to minimize the impact of security incidents.
- Compliance Measures
- Regulatory Compliance : Ensure the SIEM solution complies with relevant regulations and standards for data protection and security.
- Audit and Monitoring : Set up auditing and monitoring tools to track user activities and system changes.
Phase 5: Testing and Validation
- Functionality Testing
- Threat Simulation : Perform threat simulations to test the effectiveness of the SIEM solution in detecting and responding to various attack scenarios.
- Incident Response Testing : Validate the incident response process, including detection, alerting, containment, and remediation.
- Performance Testing
- System Performance : Ensure that the SIEM solution does not negatively impact the performance of network resources.
- Scalability Testing : Test the scalability of the SIEM solution to handle increasing amounts of log data and security events.
Phase 6: User Training and Documentation
- Training Sessions
- IT Staff Training : Conduct training sessions for IT staff on managing and maintaining the SIEM solution, including incident response procedures.
- End-User Training : Provide training for end-users on recognizing and reporting potential security threats.
- Documentation
- Configuration Documentation : Document all configurations and settings of the SIEM solution.
- User Guides : Provide user guides and troubleshooting documentation for common tasks and issues.
Phase 7: Go-Live and Post-Implementation Support
- Go-Live Preparation
- Final Checks : Perform final system checks and prepare for go-live.
- Communication : Inform users of the transition schedule and provide support contacts.
- Go-Live Execution
- System Monitoring : Monitor the system closely for any issues during the transition.
- User Support : Provide immediate support to address any issues that arise post-implementation.
- Post-Implementation Support
- Ongoing Support : Provide ongoing support and address any issues that arise post-implementation.
- System Monitoring : Implement continuous monitoring for performance and security.
Phase 8: Ongoing Monitoring and Maintenance
- Monitoring
- Threat Intelligence : Continuously update threat intelligence feeds to keep the SIEM solution updated with the latest threat information.
- Alert Management : Regularly review and manage alerts to ensure timely response to potential threats.
- Maintenance
- System Updates : Ensure the SIEM solution is kept up-to-date with the latest patches and feature updates.
- User Feedback : Gather and act on user feedback to improve the SIEM solution and its implementation.
Key Considerations
- Cost Savings : Emphasize the cost-effectiveness of using advanced SIEM solutions that provide comprehensive security monitoring at a competitive price.
- Data Privacy and Security : Ensure all configurations adhere to data privacy and security standards, especially for sensitive customer data.
- User Experience : Minimize disruption during the transition and provide comprehensive support during the go-live phase.
- Scalability : Configure the system to scale with the growth of the companies and increasing amounts of log data.
- Compliance : Maintain compliance with industry-specific regulations and standards.
By following these steps, we ensure a successful deployment of advanced SIEM solutions tailored to the needs of various customers in Sydney, providing robust, scalable, and secure security information and event management capabilities.




